SAP Identity Access Governance (IAG) is a solution that helps organizations manage the access rights of their users across different SAP and non-SAP systems. IAG enables users to request, approve, certify, and monitor access rights in a centralized and compliant manner. One of the features of IAG is privileged access management (PAM), which allows users to request and grant temporary elevated access to sensitive systems or data for a specific purpose and duration.
What is a PAM request and why is it needed?
A PAM request is a request for temporary elevated access to a system or data that is normally restricted or protected. For example, a user may need to access a production system to perform an emergency fix, or a user may need to access a confidential report to conduct an audit. A PAM request specifies the following information:
- The system or data that the user needs to access
- The reason or purpose for the access
- The duration or validity period of the access
- The approval workflow or the approvers who need to authorize the access
A PAM request is needed for several reasons, such as:
- To ensure that the access is granted only for a legitimate and justified purpose
To minimize the risk of unauthorized or inappropriate access to sensitive systems or data
To comply with the security policies and regulations of the organization and the system owner
To track and monitor the usage and activities of the privileged access
To revoke the access automatically after the validity period expires
Who can review the PAM request?
Review of PAM can be done by the user who is selected as reviewer in PAM ID maintenance.
Note – PAM review workflow users the “privilege access review” template and this cannot be changed. The Role Owner is PAM Reviewer, and the Security is the admin.
Allowed activity in PAM:
When a PAM ID is created, a Business Role needs to be assigned to it. The business role defines what activities/transactions can be used for the PAM ID.
In the definition of the PAM ID, there is also a section, Allowed Activities, for users to manually add activities/transactions of the assigned Business Role.
However, the activities manually added to this list are for PAM ID reviewer to review later and provide a reference to PAM ID creators/reviewers if they would like further to restrict allowed activities in the future.
When a user is assigned with the PAM ID and logs into the target system, the user can run all the activities defined by the Business Role of the PAM ID, which are not limited to the activities manually added the “Allowed Activities” list.
The target system will log all the activities of this PAM ID and send the log back to IAG system. Later during PAM review process, IAG system will compare the activities performed on target system with the ones manually added to “Allowed Activities” list.
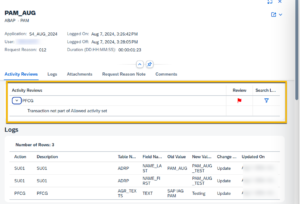
If the activity is not listed in the list, PAM review logic will give a warning saying: “Transaction not part of Allowed activity set“.
This warning message just provides a reference to PAM ID reviewer that she/he can further restrict the allowed activities via Business Role design in the future.
The reviewer can continue processing the review of the PAM ID without being blocked by this read-only waring message.
Example:
The business role has 4-Tcodes and we marked only 2 t-codes for followed activity, during the review process process – the transaction code which are not listed in allowed activity are displayed separately with the warning message.
PAM reviewer will see the below message when PAM user executes transaction which are not listed in allowed activity –