What is Risk Score?
Risk score is a numerical value that represents the level of risk associated with a user, a role, or an access request in SAP Identity Access Governance (IAG). Risk score is calculated based on the risk factors that are defined in the risk library and assigned to the relevant objects.
How Risk Score is Getting Calculated?
It is calculated by aggregating the risk factors that are applicable to a user, a role, or an access request. Each risk factor has a weight that indicates its relative importance and impact on the overall risk score.
Risk Score calculation:
The risk score formula is as follows:
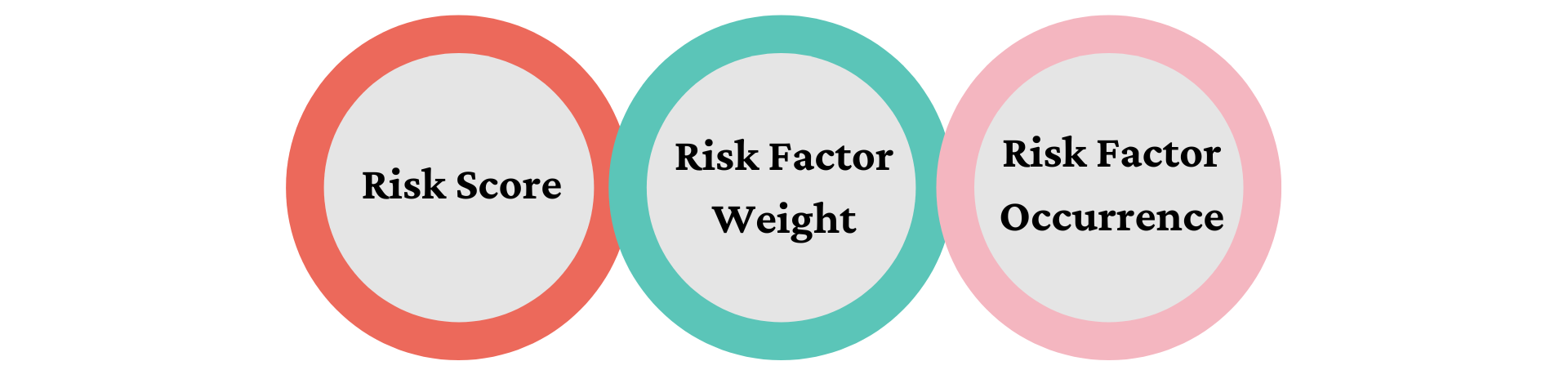
- Risk score = Sum of (risk factor weight x risk factor occurrence)
- Risk factor weight = A value between 0 and 100 that is assigned to each risk factor in the risk library
- Risk factor occurrence = The number of times a risk factor is detected for a user, a role, or an access request
For example, if a user has two roles that have the following risk factors and weights:
- Role A: SoD violation (weight = 80), Sensitive access (weight = 20)
- Role B: Excessive access (weight = 40)
Then risk score for the user is calculated as:
- Risk score = (80 x 1) + (20 x 1) + (40 x 1) = 140
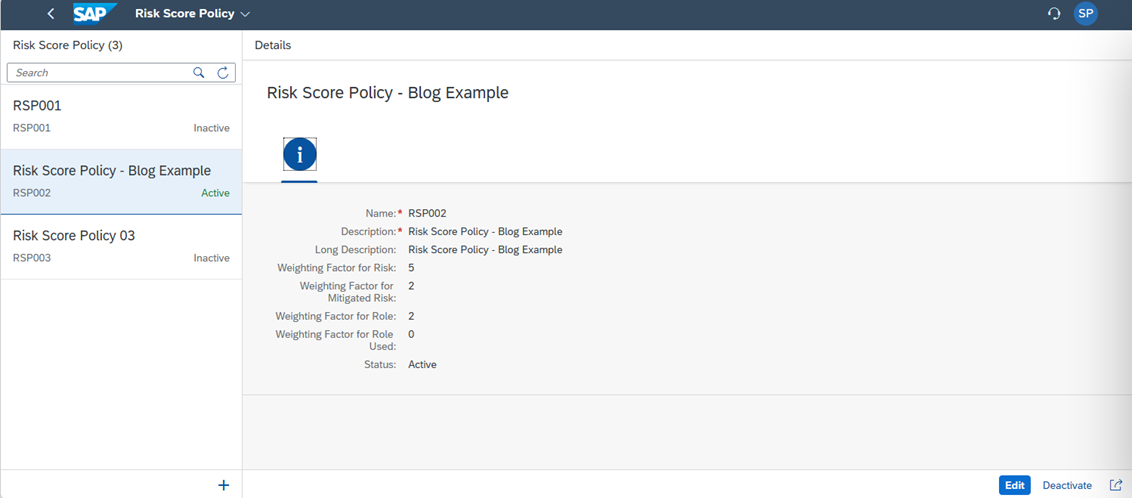
How to Create a Risk Score and view in SAP IAG?
Below steps shows how to create a risk score in SAP IAG system.
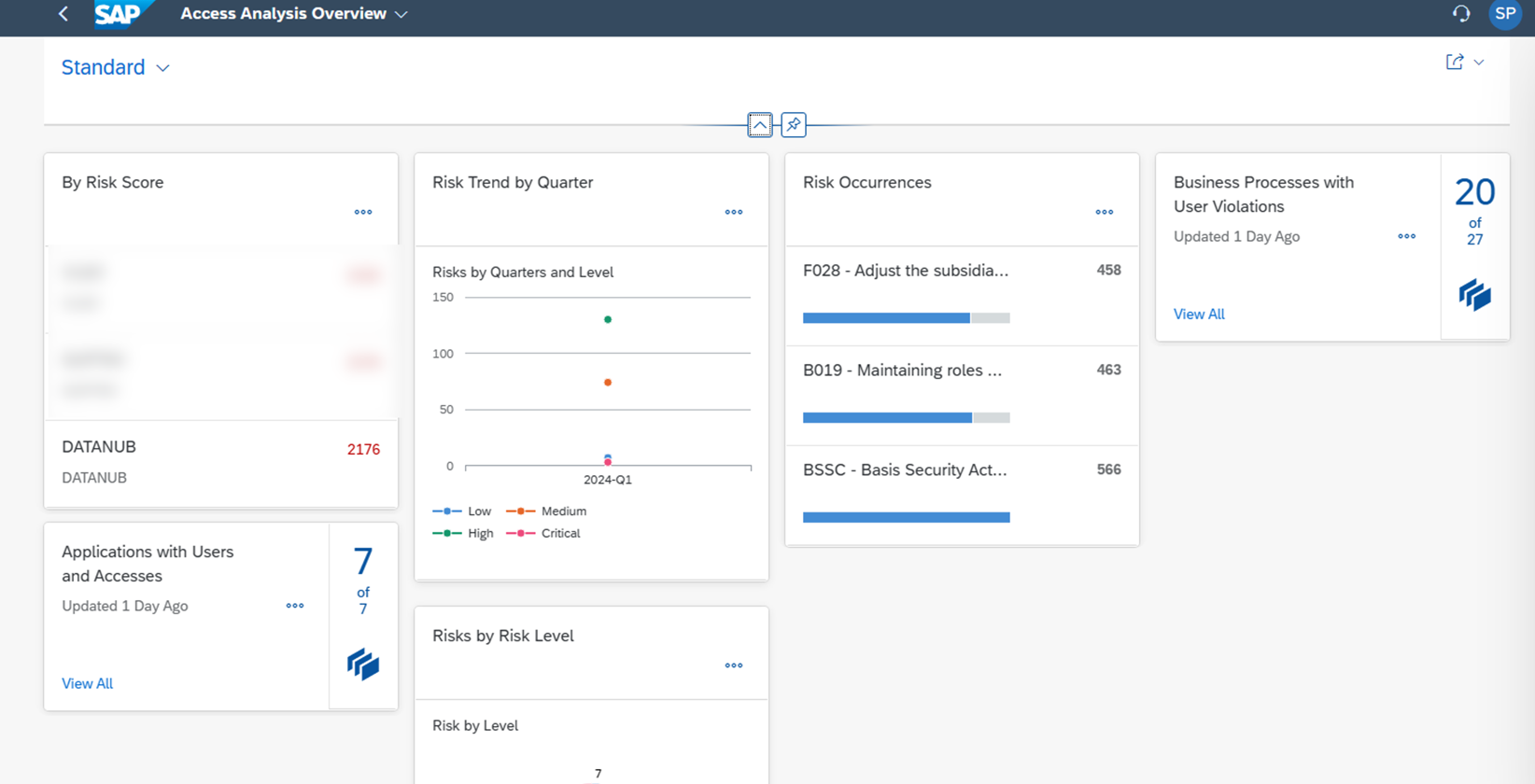
How is risk score used?
Risk score is used to measure and manage access risks in SAP IAG. Some of the use cases are:
- Risk analysis: Risk score is used to perform risk analysis on users, roles, and access requests. Risk analysis helps to identify and resolve access risks, such as SoD violations, sensitive access, or excessive access. Risk analysis can be performed on demand, periodically, or continuously.
- Risk simulation: Risk score is used to simulate the impact of adding or removing roles or entitlements on users or access requests. Risk simulation helps to evaluate and compare different access scenarios and select the optimal one.
- Risk mitigation: Risk score is used to apply risk mitigation actions on users, roles, or access requests. Risk mitigation actions include approving, rejecting, modifying, or escalating access requests, assigning or revoking roles or entitlements, or creating or updating mitigating controls.
- Risk reporting: Risk score is used to generate risk reports and dashboards that provide insights into the access risk posture of the organization. Risk reports and dashboards can be customized and scheduled according to the business needs.